Already a CyberVadis client ? You can access your account here
Know Which Vendors Are at Risk Through Our Evidence-Based Third-Party Cyber Risk Assessments
When it comes to assessing vendor risk, nothing beats the reliability and depth of an evidence-based approach. We go beyond surface-level checks with our third-party cyber risk assessments, offering a comprehensive and detailed picture of your vendors’ cybersecurity posture. That means digging into their uploaded documentation, verifying risks, and giving actionable insights—so you know exactly who meets your security standards.
CyberVadis Onboards and Supports Your Vendors at Every Step of Their Journey
We’re here to enroll your suppliers in your program and help them every step of the way, making sure your vendors have the guidance and clarity they need to complete the cyber risk assessment, and implement meaningful improvements. If your suppliers are wondering which evidence to provide or what specific actions to take, we’re here with clear, practical answers. With our expert support, your suppliers can confidently move forward, knowing they are equipped with the right knowledge and guidance to make lasting improvements.

Global Standards and Regulations are the Core of Our Methodology
ASSESSMENT VALUES
We Deliver to You and Your Vendor
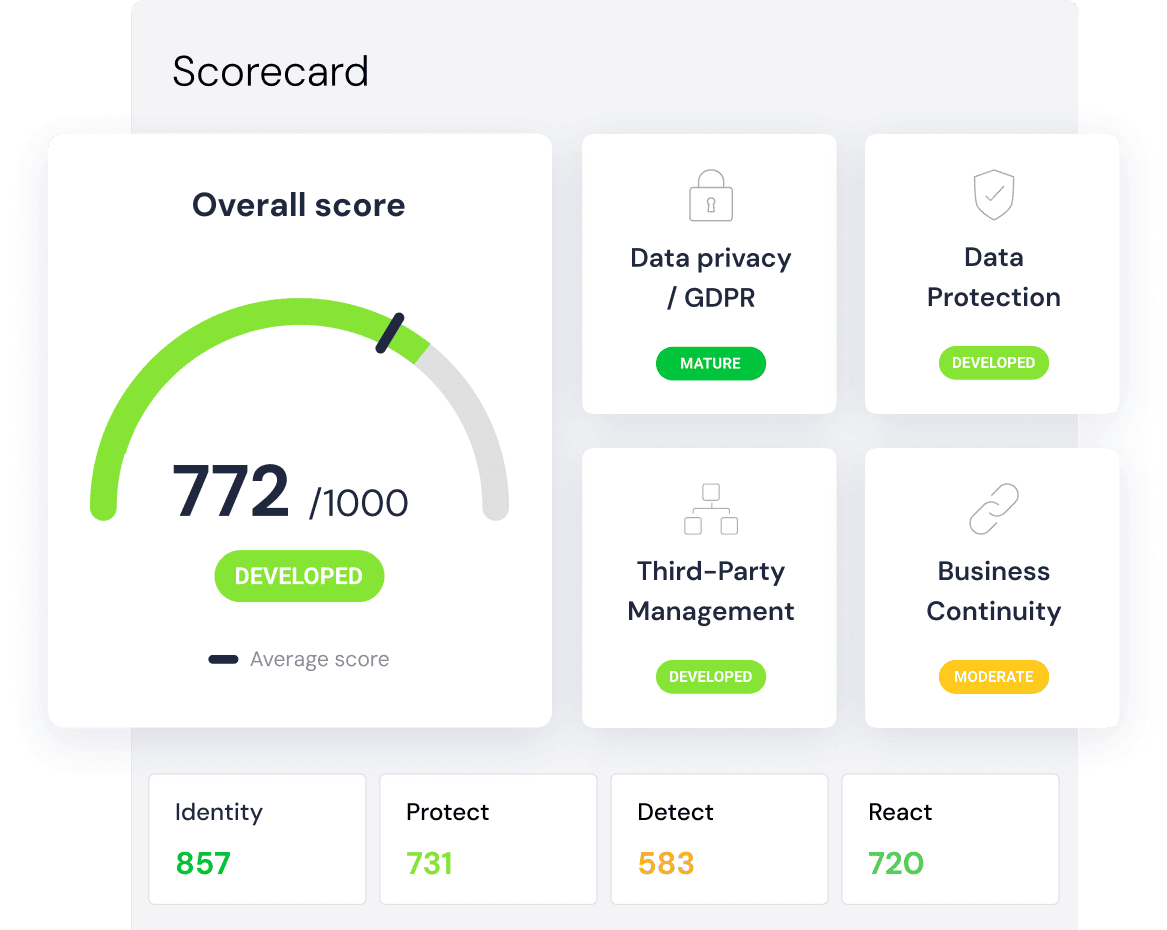
Detailed Scorecard
We evaluate your vendor’s information security management system (ISMS) and measure its maturity level by using a methodology based on globally recognized standards like ISO 27001, the NIST Cybersecurity Framework, and GDPR.
As part of our third-party risk assessment, after our experts review your vendor's questionnaire and evidence, they provide a detailed vendor evaluation scorecard, giving you clear visibility on vendor maturity, implemented controls, and aggregated scores. Vendors can also access and share their scorecards with clients and partners, benefiting all parties.
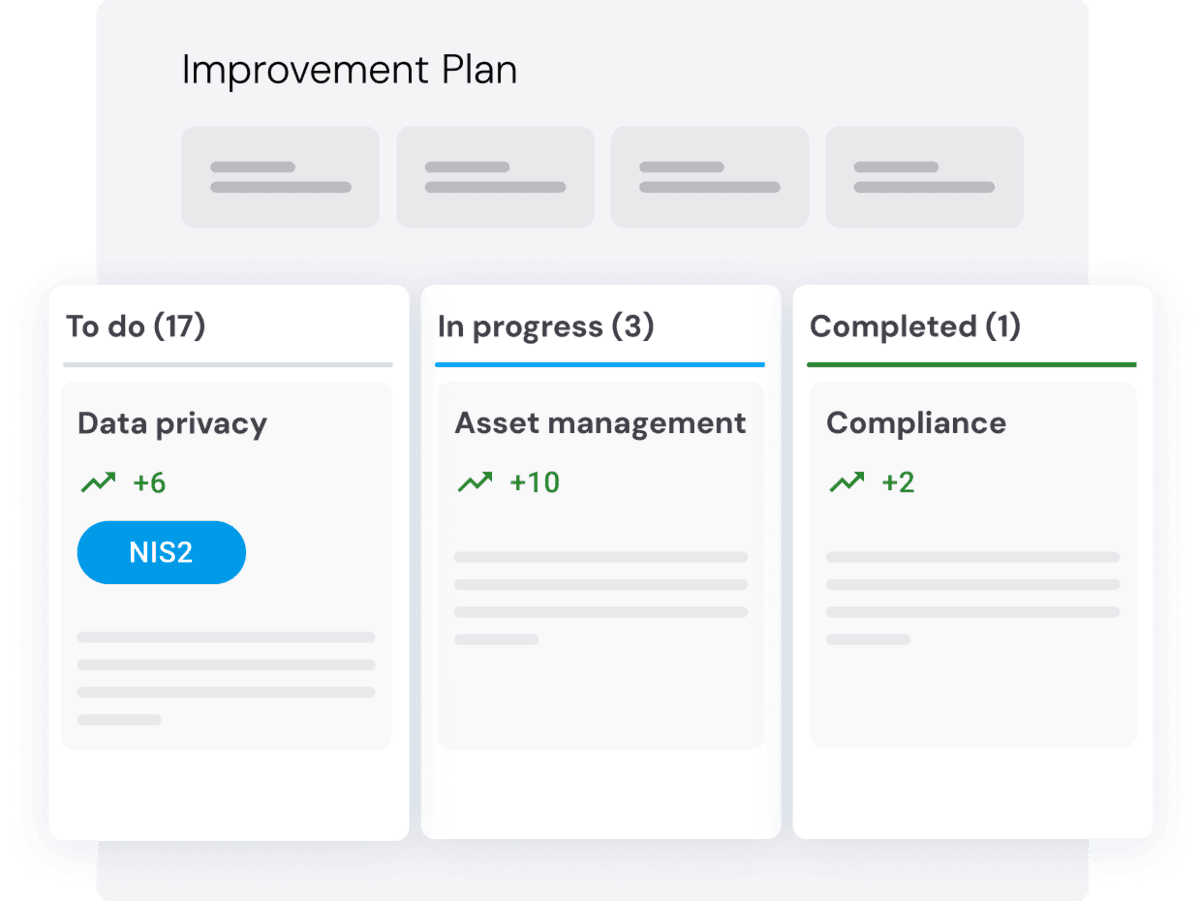
Collaborative Improvement Plan
Assessed… now what? Get a collaborative, actionable improvement plan tailored to your vendor’s profile and your company’s needs. With CyberVadis, you can prioritize critical actions, collaborate with vendors, and track progress—all on a single platform. Proactively managing third-party risk helps improve supply chain resilience, ensure compliance, and bolster overall cybersecurity by addressing cyber risks throughout your vendor ecosystem.
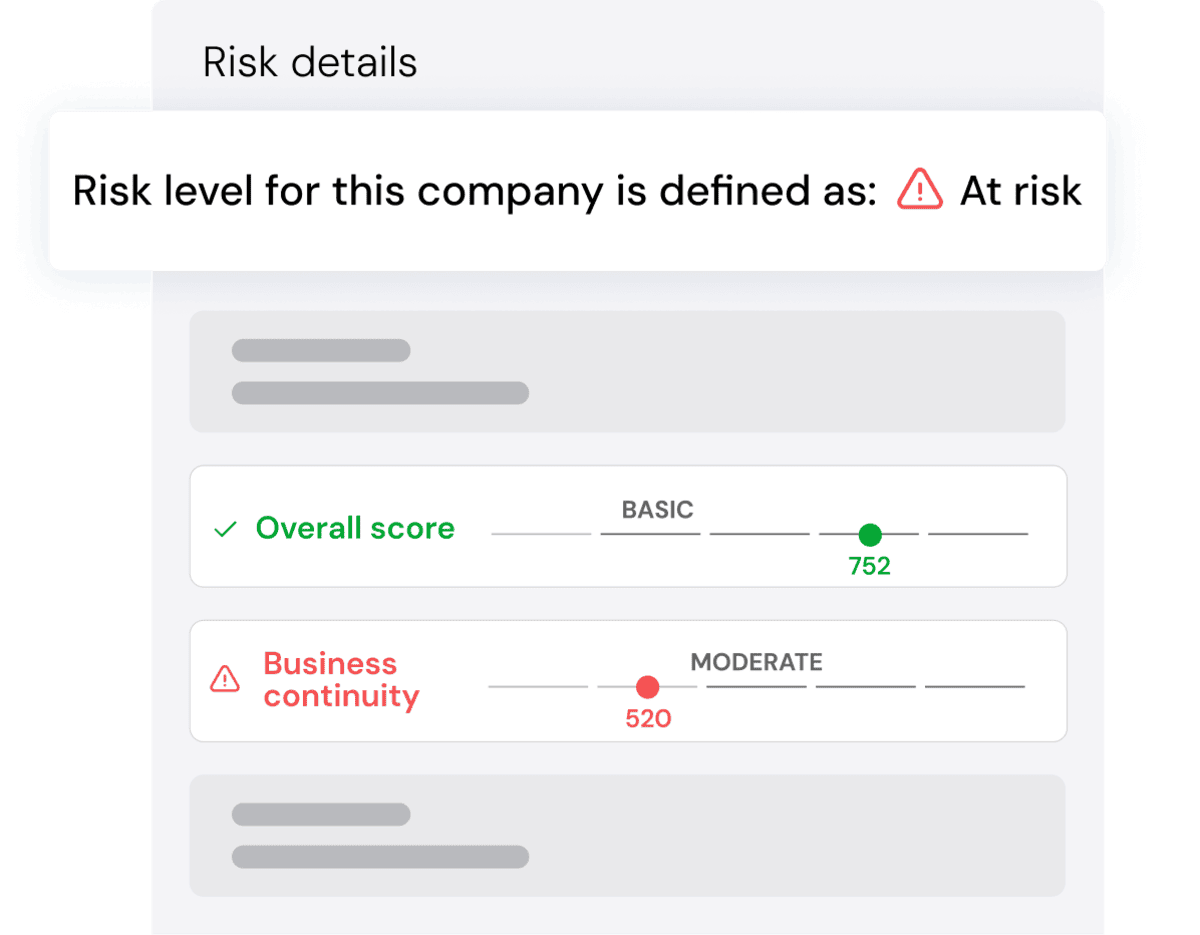
Specific Risk Level for Your Organization
Convert the results of each vendor’s maturity level assessment into specific risks for your organization, based on your relationship with the vendor and your own risk thresholds.
Learn More About CyberVadis Evidence-Based Assessments
Easily sort action items by topic like NIS2 requirements, and see exactly which ones will have the biggest impact. Improvement plans adapt to your unique needs, helping you collaborate effectively with your vendors and take meaningful steps to reduce risk—not just identify it. With third-party cyber risk management, visibility is the first step, but real security comes from mitigation.
- 1
Portfolio & Zero-touch risk insights
- 2
Evidence-Based Assessment
- 3Learn more about improvement plans
Improvement plan
Frequently Asked Questions About Third-Party Cyber Risk Assessment
Have a Question About Evidence-Based Assessments? We’d Love to Talk About It.
Got questions about evidence-based assessments or how third-party cyber risk assessments work for you and your vendors? We’re here to help you understand how these assessments can give you what your team needs to mitigate risks and have long-lasting vendor relationships.






