
Already a CyberVadis client ? You can access your account here
The Strength Behind Our Framework-Based Methodology
Our proprietary methodology combines leading international cybersecurity frameworks with expert insights and global best practices to provide standardized assessments for you and your vendors. This guarantees consistent, reliable results across industries and vendor sizes while ensuring efficiency and scalability.
Framework-based Methodology
A Methodology You Can Trust, Backed by Global Frameworks
The Standardized Assessment Your Vendors Actually Benefit From
We strike the perfect balance between thoroughness and simplicity. Our assessments fully cover key cybersecurity controls while remaining concise enough for vendors to complete without feeling overwhelmed. This way, your vendors are more likely to participate and finish, making the process smooth and effective for everyone.
Our methodology is designed to be widely accepted—by your organization, your vendors, and the industry as a whole. Built around recognized standards like NIST, ISO, and GDPR, we’ve created a standardized assessment that results in a shareable, easy-to-understand scorecard. CyberVadis’ evidence-based assessment is trusted across industries and geographies, making it simple to align with global expectations while maintaining consistency and transparency.
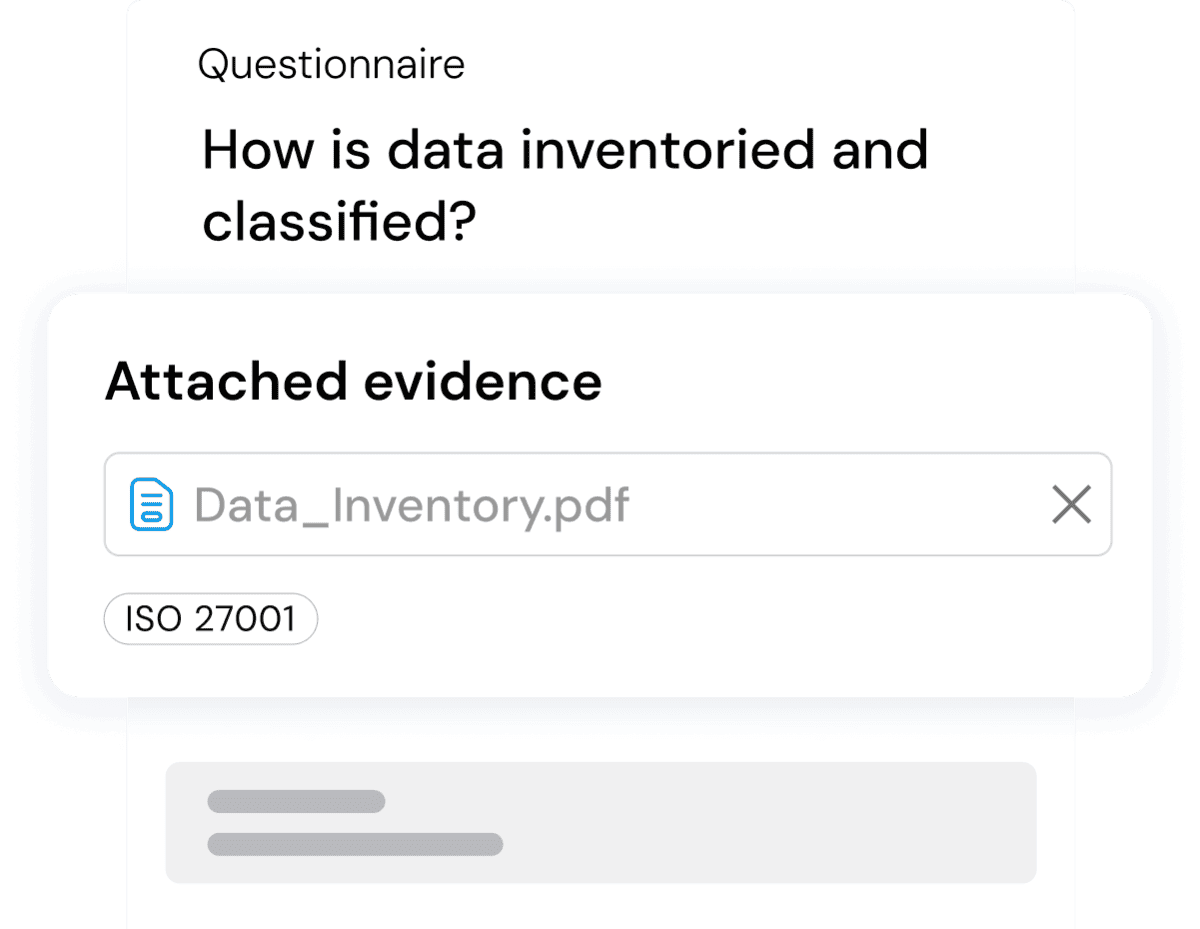
Proven Methodology Built and Maintained by the CyberVadis Experts
Our methodology evaluates a vendor's cyber maturity using key cybersecurity frameworks, including NIST, ISO 27001, GDPR, NIS2, DORA, and other relevant laws and regulations. CyberVadis assessment focuses on critical controls to ensure your supply chain remains secure and resilient against modern cyber threats.

Cyber Assessment That Fits Your Vendors
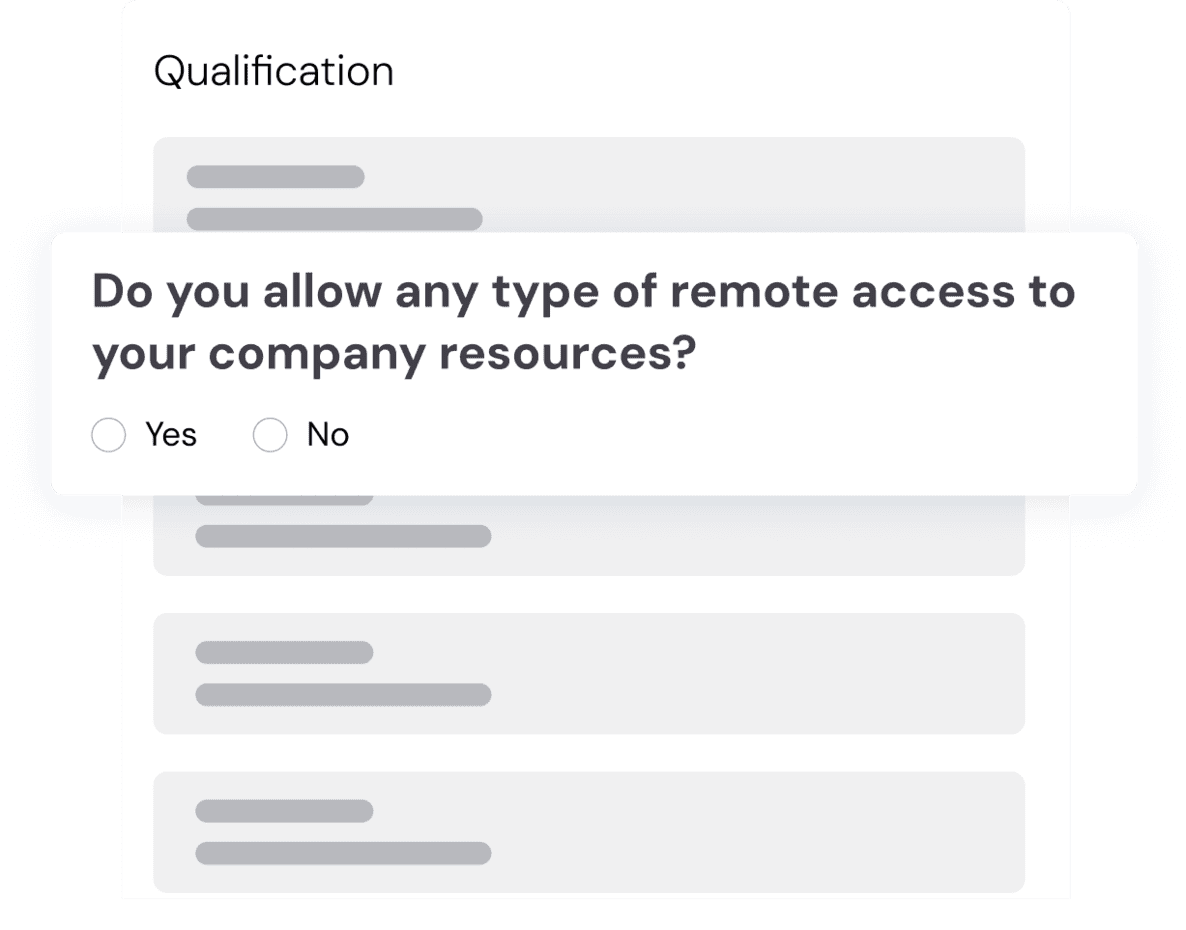
We make things easier for each of your vendors and start the assessment with a quick qualification questionnaire. By answering 10 to 15 simple questions (it only takes about 10 minutes), we ensure our questionnaire is tailored to your vendor's context including its IT practices, size, and industry.

How CyberVadis methodology maps with NIS2
Check our latest blog article to discover how CyberVadis methodology maps with NIS2 requirements to ensure your vendor’s compliance with the regulation.
Frequently Asked Questions
See CyberVadis in action
See CyberVadis in action and discover how it makes cybersecurity compliance standards simpler and more effective.






